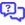Configuring global settings
NAVIGATION Global Settings
The options to configure global settings for the vPenTest account and for internal and external network penetration tests are available on the Global Settings page.
Enabling or disabling basic or advanced assessment settings
The settings saved in the Basic Assessment Settings and Advanced Assessment Settings sections on the Global Settings page determine the default settings applied to all assessments.
NOTE These sections are disabled for new vPenTest users by default.
Enabling basic settings or both basic and advanced settings adds an extra step called Settings to the scheduling wizard, which can be modified on a per-assessment basis. Refer to Steps in the scheduling wizard.
Turning the Enable Basic Settings or Enable Advanced Settings toggles on or off enables or disables those settings, respectively. If basic settings are disabled, enabling advanced settings automatically enables basic settings.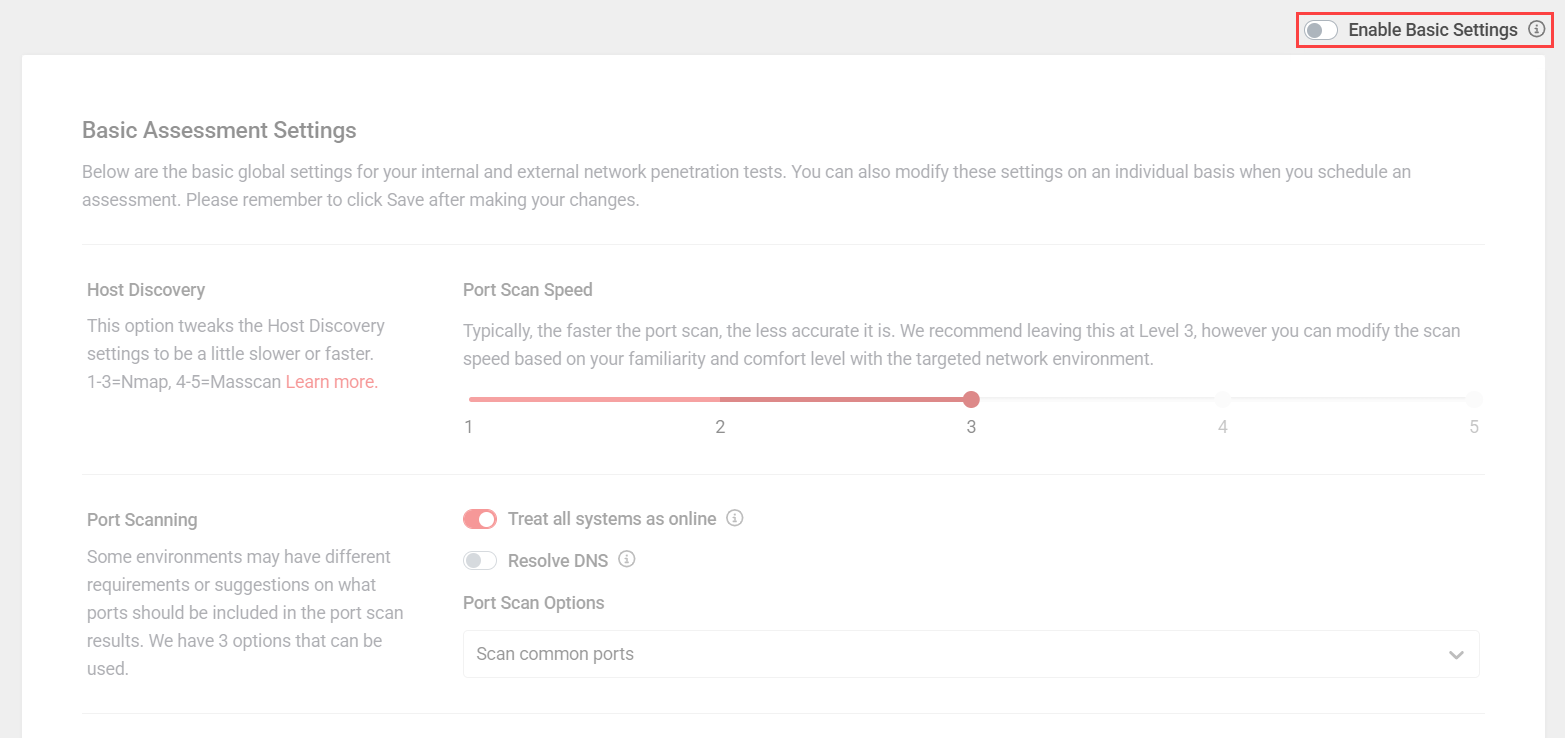
EXAMPLE This example shows the Settings step in the scheduling wizard when both basic and advanced settings are enabled.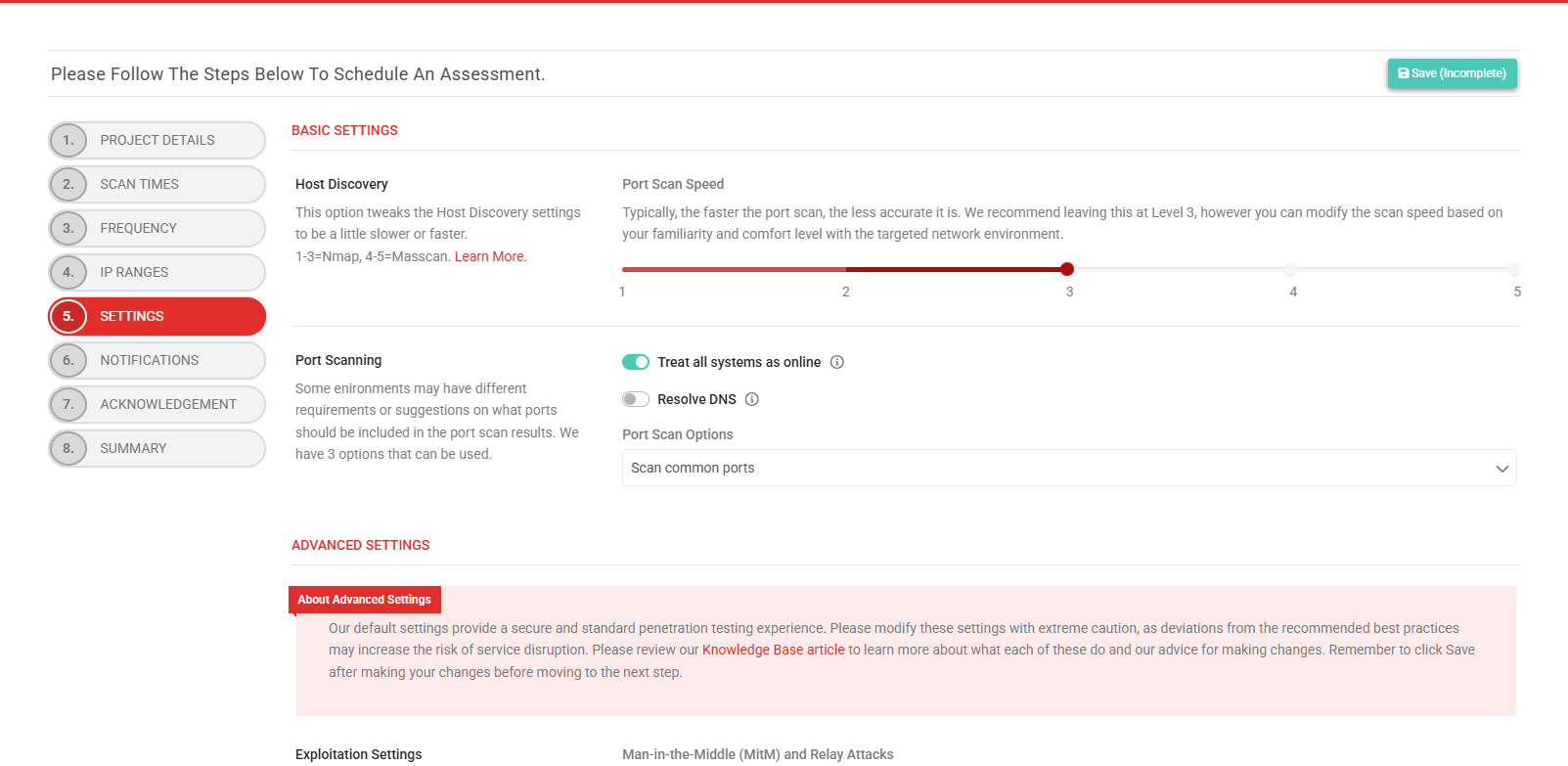
Basic Assessment Settings overview
Enabling basic settings allows you to control the host discovery process, including the port scan tool, speed, and port list. After making any changes, click Save in the lower-right corner of the section.
Explanations and recommended best practices for Basic Assessment Settings are outlined in the following drop-down sections.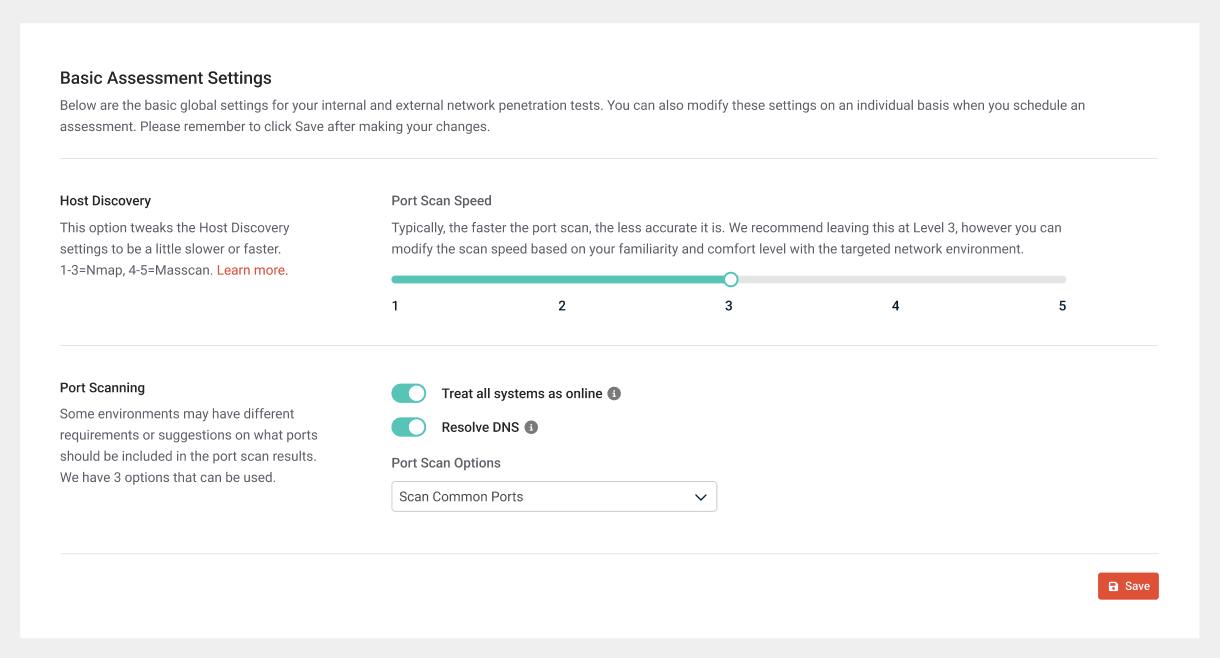
Host discovery is the process of discovering systems with open ports on the target network. Through vPenTest methodology, host discovery is performed by combining several different host discovery techniques. For details, refer to Host discovery in What is vPenTest's methodology for automated penetration testing?
Port Scan Speed
This option controls the speed of the port scanning process. The slider ranges from 1 to 5, where 1 is the slowest option and 5 is the quickest option. Typically, the faster the port scan, the less accurate it is. Any port scan speeds higher than 3 use a tool called Masscan, and speeds equal to 3 or lower use Network Mapper (Nmap).
| Port scan speed value | Scan rate | Usage |
|---|---|---|
| 1 | nmap -T1 | Port scan speeds 1 and 2 are very slow but very accurate. However, these options should be used only if the firewall is sensitive to port scans and the scope is fewer than five total IP addresses. |
| 2 | nmap -T2 | |
| 3 | nmap -T3 | Port scan speed 3 is the default option and preferred for most situations. TIP Opting to keep this value is recommended for the ideal balance between speed and accuracy. |
| 4 | masscan 1000 | Port scan speed 4 is more accurate and faster for IP ranges with 1,000 or more total IP addresses. |
| 5 | masscan 3500 | Port scan speed 5 is intended for massive IP ranges, such as /16 or 2,000 or more IP addresses. This option is very fast but less accurate. |
Once an assessment begins, settings cannot be modified manually. Required changes must be requested in a ticket opened with support@vpentest.io.
IMPORTANT Scanning all ports on all systems could significantly impact the time required for your assessment and may not necessarily provide more results than the other options.
Treat all systems as online
Turn on this toggle to treat all systems as online and ignores other host discovery techniques, such as ICMP Echo, and is equivalent to the -Pn flag in Nmap. This setting performs a ping sweep first and then port scans only the devices that respond.
Resolve DNS
Turn on this toggle to allow the host discovery process to perform DNS look-ups against each IP that it discovers as active. This can sometimes slow down the scans, depending on the environment.
Port Scan Options
When it comes to scanning ports, some environments may have different requirements or suggestions regarding what ports should be included in the port scan results. For that reason, you can select one of the following options from the drop-down menu:
- Scan common ports: Common ports refer to ports that vPenTest discovers over time. When the system is performing an assessment and detecting new ports that haven't been discovered yet, the system automatically adds those ports to the database and attributes them to a service name. This list will continue to change based on new exploits and services discovered from our assessments.
- Scan top 1000: Nmap has a built-in list of ports used for the top 1000. vPenTest simply passes this argument to Nmap or Masscan as part of the host discovery techniques.
- Scan custom ports: If you have a specific list of TCP and/or UDP ports that you'd like to scan, you can provide those ports to this feature. Although we don't provide recommendations for this option, we highly suggest developing a deep understanding of the environment before limiting the ports to a specific list. We suggest using this option only if you're looking for issues on a single port or list of specific ports. This option can also be used for a full 65K TCP port scan, but we do not recommend this option for a 65K UDP port scan. Due to the nature of UDP, attempting to do so will most likely result in the assessment halting.
Common ports
The following ports, which can be copied and pasted, are currently being scanned as part of the Scan common ports option. This list is likely to change significantly over time.
TCP
1,7,9,13,19,21,22,23,25,37,42,43,49,53,69,70,79,80,81,82,83,84,85,88,102,105,109,110,111,113,119,123,135,137,139,143,161,179,222,264,384,389,402,407,443,444,445,465,500,502,512,513,515,523,524,540,548,554,587,617,623,631,636,689,705,771,783,873,888,902,903,910,912,921,990,993,995,998,1000,1024,1030,1035,1080,1089,1090,1091,1098,1099,1100,1101,1102,1103,1128,1129,1158,1199,1211,1220,1234,1241,1270,1300,1311,1352,1433,1440,1468,1494,1521,1530,1533,1581,1582,1583,1604,1723,1755,1811,1883,1900,2000,2049,2082,2083,2100,2103,2121,2181,2199,2207,2222,2323,2362,2375,2376,2379,2380,2381,2525,2533,2598,2601,2604,2638,2809,2947,2967,3000,3037,3050,3057,3128,3200,3217,3268,3269,3273,3299,3300,3306,3311,3312,3351,3389,3460,3500,3628,3632,3690,3780,3790,3817,4000,4092,4322,4343,4369,4433,4443,4444,4445,4567,4659,4679,4730,4786,4840,4848,5000,5022,5037,5038,5040,5051,5061,5093,5168,5222,5247,5250,5275,5347,5351,5353,5355,5392,5400,5405,5432,5433,5498,5520,5521,5554,5555,5560,5580,5601,5631,5632,5666,5671,5672,5683,5800,5814,5900,5920,5938,5984,5985,5986,5988,5989,6000,6001,6002,6050,6060,6070,6080,6082,6101,6106,6112,6262,6379,6405,6502,6503,6504,6514,6542,6556,6660,6661,6667,6905,6988,7000,7001,7021,7071,7077,7080,7100,7144,7181,7210,7373,7443,7474,7510,7547,7579,7580,7676,7700,7770,7777,7778,7787,7800,7801,7879,7902,8000,8009,8012,8014,8020,8023,8028,8030,8080,8081,8086,8087,8088,8089,8090,8095,8098,8099,8127,8161,8180,8205,8222,8300,8303,8333,8400,8443,8471,8488,8500,8503,8545,8554,8686,8787,8800,8812,8834,8880,8883,8888,8899,8901,8902,8903,8983,9000,9001,9002,9042,9060,9080,9081,9084,9090,9091,9092,9099,9100,9111,9152,9160,9200,9300,9380,9390,9391,9418,9440,9443,9471,9495,9524,9527,9530,9595,9600,9809,9855,9999,10000,10001,10008,10050,10051,10080,10098,10162,10202,10203,10443,10616,10628,11000,11099,11211,11234,11333,12174,12203,12221,12345,12397,12401,13364,13500,13838,14330,15200,15671,15672,16102,16992,16993,17185,17200,17472,17775,17776,17777,17778,17781,17782,17783,17784,17790,17791,17798,18264,18881,19300,19810,19888,20000,20010,20031,20034,20101,20111,20171,20222,20293,22222,23472,23791,23943,25000,25025,25565,25672,26000,26122,27000,27017,27019,27080,27888,28017,28222,28784,30000,31001,31099,32764,32913,34205,34443,34962,34963,34964,37718,37777,37890,37891,37892,38008,38010,38080,38102,38292,40007,40317,41025,41080,41523,41524,44334,44818,45230,46823,46824,47001,47002,48899,49152,50000,50002,50013,50070,50090,52302,52311,55553,55580,57772,61616,62078,62514,65535UDP
161,500,623,5351Advanced Assessment Settings overview
IMPORTANT Customizing the following settings may lead to severe business, network, or user disruption. The default settings have been thoroughly tested to prevent disruption. We highly recommend using our default options for most situations, which can be applied any time by clicking Restore Default Settings in the upper-right corner of the section. Changes should be made with extreme caution and only for specific reasons.
The advanced settings in vPenTest are designed to offer you more control over the focus and aggressiveness of your penetration testing. After making any changes, click Save in the lower-right corner of the section.
Explanations and recommended best practices for Advanced Assessment Settings are outlined in the following drop-down sections.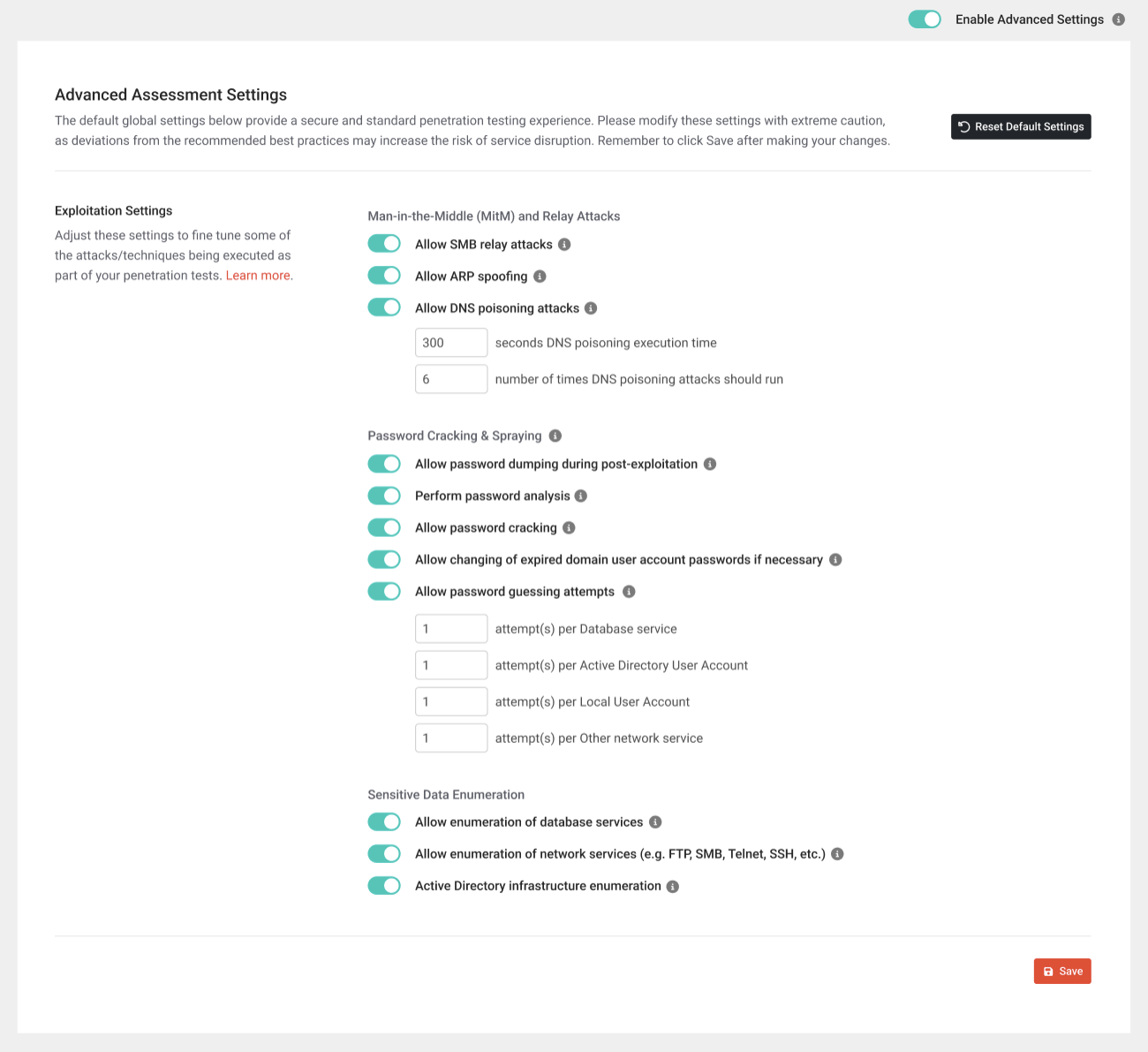
Grey Box Pentesting
In the scheduling wizard, the Grey Box Pentesting toggle is displayed at the top of the Advanced Settings section when scheduling an internal assessment. Compromised Microsoft AD/local credentials are a significant security risk. This feature helps organizations assess the real-world impact of stolen or phished credentials, ensuring they can proactively mitigate threats before they become breaches. Refer to Grey Box Internal Penetration Testing to learn more.
Exploitation Settings
For the beginning stages of the customized exploitation settings, the following options are available to help fine tune some of the attacks/techniques executed as part of a penetration test. These options allow you to tailor these attacks to specific organizations, allowing you to perform a more comprehensive test while taking into consideration security controls and settings within the targeted organization.
Allow SMB relay attacks
- SMB relay attacks occur when one system attempts to authenticate another system via SMB, and that targeted system takes the request and relays it to another system.
- When enabled, vPenTest will attempt to take any authentication attempts it receives from systems on the network and relay them to other targets.
- This could allow vPenTest to piggyback off a user’s authentication request, allowing vPenTest to authenticate targets without any knowledge of credentials since it is taking an incoming connection and relaying it to another system.
Allow ARP spoofing
- ARP poisoning attacks occur when an attacker’s system tricks one or more systems on the local subnet into believing that the MAC address to reach a legitimate target is now the attacking system’s MAC address.
- This allows for the interception of traffic, which then allows for the inspection of traffic for sensitive data.
- When enabled, vPenTest will attempt to perform ARP spoofing attacks between two targets at a time.
- Once this test is completed, the ARP entries are restored to their original values.
Allow DNS poisoning attacks
- DNS poisoning attacks occur when an attacking machine attempts to trick a system into believing that the DNS name in question actually belongs to the attacking machine instead of the legitimate target.
- When successfully exploited, vPenTest can capture and relay credentials between multiple systems.
- To execute this attack safely, the number of seconds that DNS poisoning is run should be relatively low; however, the number of times the attack runs can be more flexible.
Allow password dumping during post-exploitation
- When enabled, vPenTest will attempt to dump cleartext and/or hashed credentials from memory and other services within the compromised system. These passwords may be used to conduct post-exploitation.
- Disabling this functionality could significantly impact the value and results of the penetration test.
Perform password analysis
- If vPenTest is able to recover a list of cleartext credentials (either through password dumping or cracking), then vPenTest will automatically perform a quick password analysis on the compromised credentials.
- The results will be incorporated into the technical report to show some of the statistics on cracked passwords (for example, average length of passwords, whether or not passwords use uppercase/lowercase letters, and so forth).
- Ultimately, this can provide some information about the strength of the organization's password policy
NOTE This option is only possible if vPenTest is allowed to perform password dumping during post exploitation, which is why if you enable Allow password dumping during post-exploitation, this option is also enabled by default.
Allow password cracking
- When vPenTest successfully acquires password hashes, this option permits vPenTest to initiate password-cracking attempts. Whenever a cleartext credential is obtained from this process, vPenTest will attempt to escalate privileges and identity with additional valuable data. Disabling this feature considerably limits the effectiveness and overall utility of post-exploitation activities.
Allow changing of expired domain user account passwords if necessary
- In some cases, when vPenTest successfully obtains access to a valid cleartext credential, it may be determined that the password has expired.
- By enabling this option, vPenTest will attempt to change the password to a random complex password for the sake of being able to leverage the compromised credentials during post-exploitation.
Allow password guessing attempts
- When enabled, vPenTest will attempt to perform login attempts across various services within the environment.
- Once valid credentials are found, vPenTest then leverages these to try to gain further access to sensitive data or the environment.
- Attempt(s) per Active Directory User Account
IMPORTANT Setting this option to a relatively high number will result in account lockouts if the password policy for the domain limits the number of login attempts. Make sure to input a value less than the password policy.
NOTE These password attack thresholds are on a per-user basis.
EXAMPLE Suppose the value for Active Directory User Account is set to 4. In that case, vPenTest will perform four password attempts per Active Directory domain user account that it discovers during testing.
Allow enumeration of database services
- If vPenTest is able to establish access to credentials that provide sufficient access to database services, this option provides authorization to leverage the credentials to attempt to find sensitive information within the database content.
Allow enumeration of network services (e.g. FTP, SSH, NFS etc.)
- If vPenTest is able to compromise user or service account credentials, it will use them to attempt to gain access to various network services, such as SMB shares, FTP/Telnet/SSH servers, and so forth.
- Once accessed, vPenTest will attempt to extract sensitive data from the compromised service(s).
Active Directory infrastructure enumeration
- When possible, vPenTest will attempt to enumerate as much information from Active Directory to use during post-exploitation.
- Information such as domain user accounts, group memberships, trusts, account lockout policies, and so forth.
- Disabling this feature could significantly impact the value and results of the penetration test.