Grey box internal penetration testing
Overview
Compromised credentials are a significant security risk. This feature helps organizations assess the real-world impact of stolen or misused Microsoft Windows credentials, ensuring they can proactively mitigate threats before they become breaches.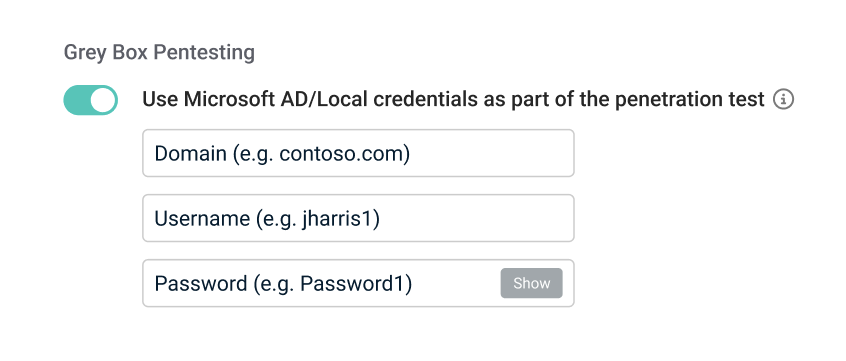
Purpose
vPenTest will utilize the supplied credentials to:
-
Move laterally, escalate privilege and hunt for sensitive data.
-
Highlight deficiencies in user permissions and privilege management through privileged escalation attempts.
-
Provide actionable insights to improve security posture.
What credentials work?
-
Microsoft local user account
-
Microsoft AD domain user account
NOTE To get the most out of this feature, we encourage you to provide the typical, everyday user account as opposed to elevated privileges. By providing credentials with elevated privileges, such as a domain administrator, the results will not accurately represent the potential impact of a typical user account compromise.
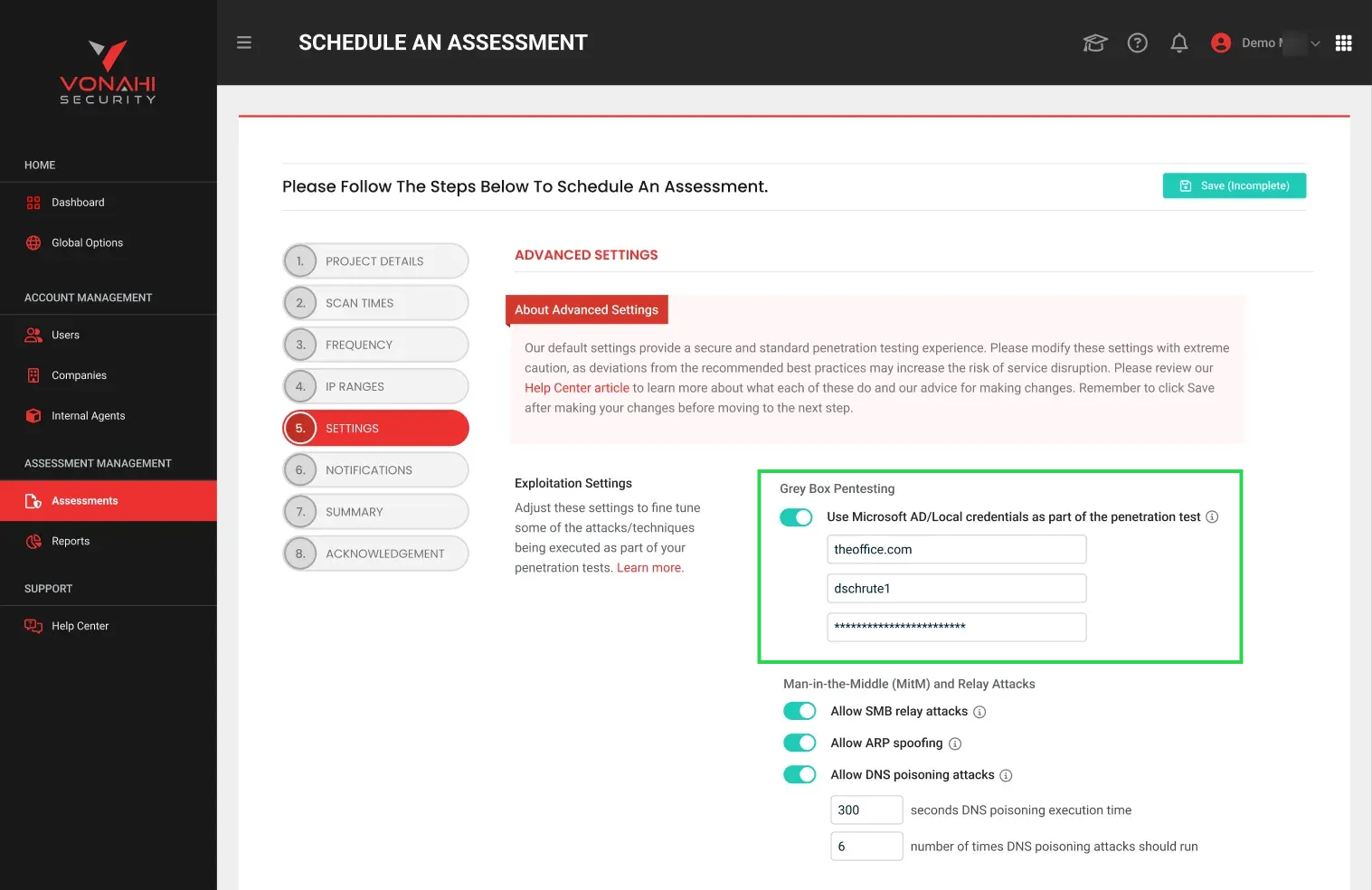
Enabling grey box testing
Prerequisites
The option to enable Grey Box Testing will appear in the Scheduled Assessment Wizard under the following conditions:
-
Advanced Settings must be enabled.
-
An internal assessment type must selected:
-
Internal Network Penetration Test
-
Internal Network Prospecting Test (MSPs on IP pool licensing)
-
Configuration steps
Navigate to Scheduled Assessment Wizard > Settings Step > Advanced Settings.
-
Toggle Use Microsoft AD/Local credentials as part of the penetration test. (Default is Off).
-
Upon enabling, three input fields will appear:
-
Domain (e.g.,domain.com)
-
Username (e.g., jharris1)
-
Password (e.g., Password1) (masked by default, with an option to view cleartext only during a new assessment setup)
-
If users return to edit an existing scheduled assessment, the password will remain permanently masked.
-
All stored credentials are encrypted and masked to prevent exposure.
-
-
IMPORTANT Credentials for in-progress assessments cannot be modified. Changes to the credentials in scheduled assessments will only affect assessments that start after the change.
During the pentest
-
Credential validation:
-
vPenTest will attempt to authenticate using the provided credentials.
-
If the credentials are invalid, the following will take place:
-
An activity log message will appear in the assessment, indicating that the provided credentials are invalid.
-
The assessment narrative will contain text that explains that the provided credentials were tested and confirmed to be invalid.
-
vPenTest will continue the assessment as usual, by leveraging other credentials, if possible.
-
-
-
Post-exploitation prioritization:
-
If valid, vPenTest will prioritize these credentials for deeper post-exploitation analysis.
-
The final report will clearly state that these credentials were provided by the client rather than obtained during the pentest process.
-
Best practices
1. Matching credentials with the target environment
Ensure the credentials you provide correspond to systems that are present and accessible in the target environment.
-
Providing Active Directory credentials for user@organization.local when you have Windows domain-joined systems accessible via SMB (port 445).
-
Providing Microsoft 365 credentials (like
admin@organization.onmicrosoft.com) when the internal systems use a different domain (likecontoso.local). -
Providing domain credentials when no systems have SMB (port 445) or Kerberos (port 88) open or accessible.
2. Providing appropriate access levels
The level of access provided affects the potential impact demonstrated by the assessment. We recommend providing credentials equivalent to what an everyday user would have in the target environment.
-
For Active Directory environments: A standard domain user with typical access to common resources, similar to what the average employee would use daily.
-
Providing domain administrator or highly privileged credentials.
Common pitfalls to avoid
-
Domain Mismatch: Providing credentials for a domain that doesn't match the internal domain environment (e.g., providing
user@organization.onmicrosoft.comwhen internal systems usecontoso.local). -
Network Accessibility: Providing domain credentials when no systems with authentication services (like SMB on port 445 or Kerberos on port 88) are accessible to our testers.
-
Expired or Invalid Credentials: Providing temporary credentials that expire during the testing period.