How does the vPenTest VM stay updated?
Overview
This document provides information about how the continuous penetration testing service performs updates to ensure security and patching of the VM.
The penetration testing appliance/VM is broken down into two separate components:
- Virtual Machine / Physical Appliance: This is the physical or virtual machine that we require Ubuntu to be installed on. The penetration test does not execute from the tools native to the virtual machine. There are no penetration testing tools installed on the VM without the docker container.
- Docker Container: The docker container is a layer of tools that sits on top of the Virtual Machine only for the duration of the penetration test. Afterwards, this container is wiped and removed from the virtual machine.
Virtual Machine (VM)
To maintain patches on the VM, it is requested that the installer enable automatic updates. This information is requested from within vPenTest Agent Installation Guide in step 24, as follows:
- Step 24: Once you click Yes on the screen above, the installation of the operating system will take place. After it’s completed, you’ll be prompted to select how often you want to run updates. You can choose Install security updates automatically, as shown:
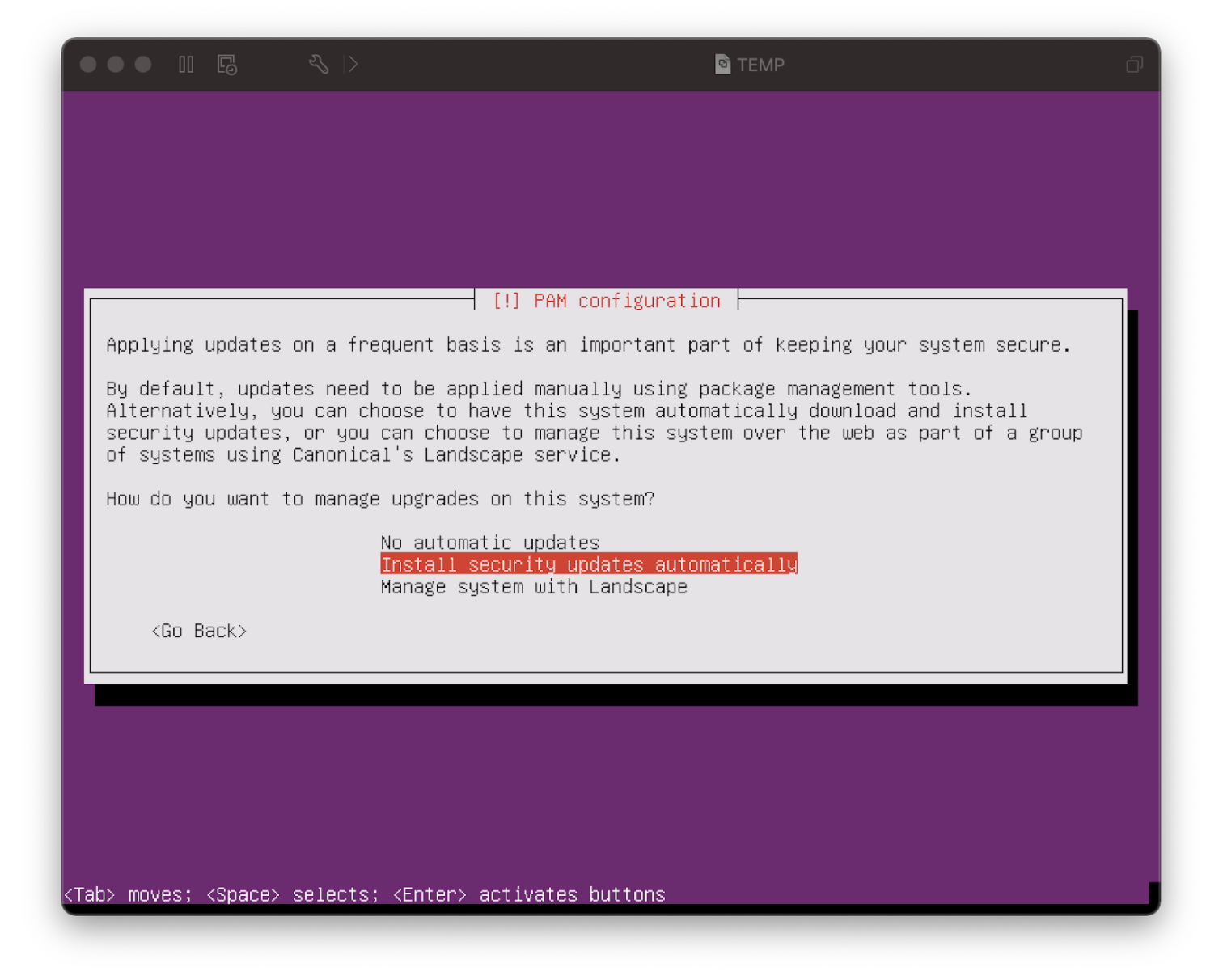
As such, the Ubuntu VM should be installed to automatically install and apply security patches. While the VM may periodically have updates suggested upon logon, these are typically non-security related.
As mentioned in Ubuntu’s article, some environments may not necessarily want to have automatic updates installed due to security concerns. In these alternative scenarios, the VM can be safely turned off or destroyed when it is not required for a penetration test. When the VM is turned back on, it will fetch and apply security updates per its automatic update policy.
Docker Container
The docker container is maintained automatically in AWS without any manual intervention. Every 12 hours, the AWS code pipeline performs the following tasks:
- Pulls the latest kali docker container.
- Adds custom tools and scripts on top of it (developed in-house).
- Runs updates to apply the latest tools, packages, and security updates.
- All of the tools used for the penetration test are automatically tested.